Security testing is one of the key aspects to test when it comes to software related to banking, website hosting, e-commerce website or applications, etc. To carry out security testing is challenging since tester has to consider all the areas which could act as an entry point or loopholes for hackers or illicit users. Here, instead of checking the functionality, testing is more focused on breaking it and test its safety and security under normal and abnormal circumstances. In this article, we are going to discuss Types Of Security Testing and the fundamentals of security testing to understand it in a better way.
Tester Has To Test Following Attributes In Security Testing:
- Authentication: In this attribute, digital identification of a user is tested and verified. For example, when you login to your email service, you need a valid and unique combination of username and password, when you enter the right one, you are allowed to enter the inbox but if you entered either of them wrong, you will not be allowed to access your emails. This is authentication process. It confirms that the user is authentic and validated to use the service.
- Authorization: This attribute ensures that the user or program is authorized to make any changes or to see the contents in a software application. Here user and its access rights are thoroughly tested. For example, in your office PC if you are not admin then you will not be allowed to make changes or download programs yourself. You will need admin rights (or Admin username and password) to do so. When you are authorized to do modifications, you can do it.
- Availability: As name says, this tests the availability of the software application i.e. it is always up and running, information and services are available whenever needed. Also, this includes the backup files which are readily available of any failure occurs.
- Confidentiality: This ensures that information and services are available to the intended users and only shown when requested. In this particular attribute penetration testing is done and all the defects found in that testing are fixed. This testing will be discussed in later part of this article.
- Integrity: This ensures that information provided to the user is correct and updated.
Security testing must be started at an early stage to minimize defects and cost of quality. It is a good practice to start security testing at the time of requirement gathering, this ensures that quality of the end product will be high. Relation between SDLC and security testing is shown below in a diagrammatic form:
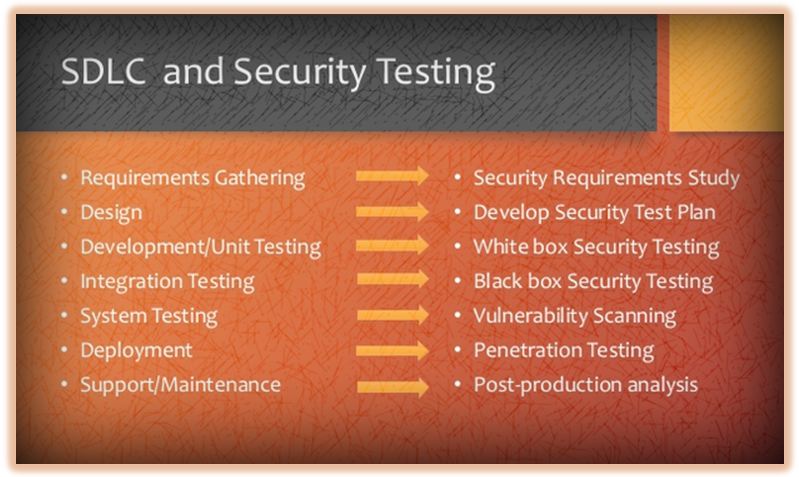
Types Of Security Testing:
Let’s now talk about the types of security testing. There are six types of security testing performed on an application. I have explained them in brief below:
- Vulnerability scanning: in this testing, whole system under test is scanned to find out the loopholes and vulnerable signatures.
- Penetration testing: an attack from hacker is simulated on the system under test. Like I have mentioned before, security testing is the one in which tester has to think of destroying the system while testing it. Penetration testing is one such example.
- Ethical hacking: This is different from penetration testing since here system under test is attacked from within to expose all the security flaws and loopholes in the application or software.
- Risk assessment: the assessment of risk involved with the security of system under test is done and then risks are classified as High, Medium and Low based on certain factors.
- Security scanning: This scans the whole system under test and finds out the network weaknesses. Then they are studied in detail, analyzed and fixed.
- Security review: As name suggests, this is the review process for security standards. Whether all the standards are followed and implemented properly are checked through gap analysis and code or design reviews.
These were some of the types of security testing being followed in different organizations. There is no standard way to test the security of an application, it purely depends on the purpose it serves and what are the security risks involved in it. Always start security testing by testing the user interfaces, this is the first place of entry for hackers and illicit users. Then think what a hacker would probably do if he gets the access or entry to the system, whether he is going to steal credit card info or access some confidential files etc. start some destructive testing i.e. to test what application or system cannot do and then pay attention to the error messages you get. Once you are done with all these types of testing, try and dig deeper and see what could be the loopholes when it comes to security at the code level. With some experience, you will be able to perform security testing better.
Conclusion:
If you have more to add on this then feel free to add in the comments section below. Also please let me know your thoughts and feedback. All you experienced Security testers out there, please add your experiences that will definitely help all fresher testing friends.
⇓ Subscribe Us ⇓
If you are not regular reader of this website then highly recommends you to Sign up for our free email newsletter!! Sign up just providing your email address below:
Happy Testing!!!
- Seven attributes of Security Testing
- Security Testing approach for Web Application Testing
- What all points to be considered in Security Testing?
- Automation Is A Must In Web Application Security Testing
- How To Do Security Testing Using SoapUI?
- Understand SQL Injection Better with the SQL Injection Cheat Sheet
- Model Based Testing: Testing Type You Must Know!
- What is Configuration Testing In Software Testing?
- Is Crowdsourcing Good For Quality Assurance?
- Pairwise Testing in Software Testing

6 thoughts on “Attributes And Types Of Security Testing – Basic Fundamentals”
This is good article, i get all information on basics of security testing. thanks a lot
Clear explanation on Basics of security testing.
I really liked the points mentioned under Types Of Security Testing section. thanks :)
My manager ask me to execute the smoke testing on application. I am fresher in testing, can someone please tell me about smoke testing. It would be great if I get documentation as well.
Excellent article. Many times I think of working of Security testing, however not got a chance to work on. Thanks for this article to understand basic concepts of Security testing.
nice artical…thanks
Thanks for your efforts. Cleared my basic fundamentals of Security testing.