What is Security Testing?
Security testing is one of the most important types of software testing intended to find the vulnerabilities or weaknesses of the software application. The main objective of security testing is to find the vulnerabilities of the system & determine that its data and resources are protected from possible intruders. Security testing allows us to identify the confidential data stays confidential or not.
Now a day’s online transaction is rapidly increasing, so security testing for web application is one of the most important things to be carried out while testing web applications. Security testing is to be carried out once the system is developed & installed. To identify the vulnerabilities the network security testing should be performed periodically.
There are “Seven attributes of Security Testing” as follows, for more details check here:
- Authentication
- Authorization
- Confidentiality
- Availability
- Integrity
- Non-repudiation
- Resilience
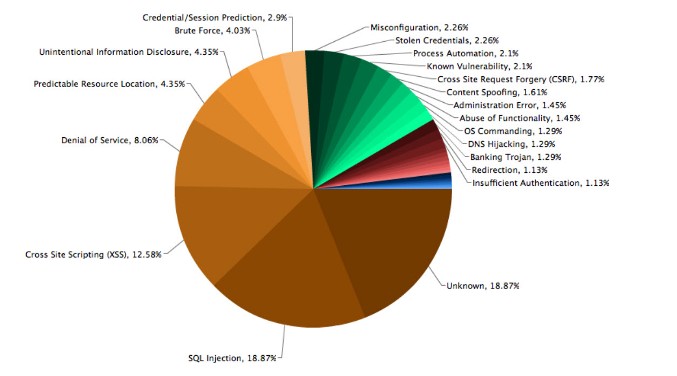
In the pie-chart below, created by the Web Hacking Incident Database for 2011 (WHID) clearly shows that whilst many different attack methods exist, SQL injection and XSS are the most popular.
Image Credit: @acunetix.com
6 basics terms used in Security Testing
Here are the useful terms frequently used in severity testing:
What is “Penetration Testing”?
Penetration testing is a type of security testing process to identify security vulnerabilities in an application by evaluating the system or network with various malicious techniques. The main purpose of this testing is to protect the identified vulnerabilities & secure the important data from unknown users who do not have access to the system like hackers. The penetration testing can be carried out after the cautious consideration, notification, and planning.
There are two types of penetration testing, White box testing & Black box testing. In White box testing is all information is with tester prior start testing like IP Address, Code & Infrastructure diagram & based on available information tester will perform the testing. In Black box testing, tester does not have any information of system under test. This is a more accurate testing method as we are simulating the testing with real hackers which they do not have the information of the existing system.
Password cracking
In security testing for web applications Password cracking programs can be used to identify weak passwords. It can start using guessing the common username and password or the use of a password cracking tool. Password cracking confirms that users are making use of adequately strong passwords.
In the system password are generally stored in the encrypted format like hash, so once they use try to login using login credentials then hash is created for newly entered password & compared with the originally stored hash, once the stored hash matches then the user is authenticated. Automated Password cracking is basically generated the random hashes unless and until a match is not found. The most commonly used password cracking is the use of the Dictionary attack. In this case, the automated tool is trying all words from the dictionary.
It would be easier if the password does not ask for complex passwords like password must having at least one digit one character and one special character etc. Sometimes the passwords are stored on cookies if such login credentials information stored without encryption in cookies then the hacker can use different methods to get the username & password information.
What is “Vulnerability”?
Vulnerability is a weakness in a system under test which may cause malicious attaches by unauthorized users. The vulnerability can be increase due to bugs in the software, lacking Security testing or viruses, etc. These security vulnerabilities require patches, or fixes, in order to prevent the potential for compromised integrity by hackers or malware.
What is “URL manipulation”?
URL Manipulation is very much interesting and most common type of attack by hackers. In this attack, the hackers manipulate the website URL query strings & capture the important information.
This happens when the application uses the HTTP GET method to pass information between the client and the server. The information is passed in parameters in the query string. The tester can modify a parameter value in the query string to check if the server accepts it.
Via HTTP GET requests user information is passed to the server for authentication or fetching data. An attacker can manipulate every input variable passed from this GET request to the server in order to get the required information or to corrupt the data. In such conditions, any unusual behavior by application or web server is the doorway for the attacker to get into the application.
So while security testing the URL manipulation test cases should be considered to make sure that using URL manipulation unauthorized user is not able to access the important information or not corrupting the database records.
What is “SQL injection”?
SQL Injection is one of the most common application layer attack techniques used by hackers. SQL Injection is one of several web attack mechanisms used by hackers to steal data from organizations. SQL injection attacks are very critical as the attacker can get vital information from the server database. It is a type of attack which takes the advantage of loopholes present in the implementation of a web application that allows a hacker to hack the system like passing SQL queries into all input fields and tries to hack the system.
Hackers try to query the database with SQL injection statements or part of SQL statement as user input & pull out the vital information from the system or crash the system & from the error displayed on the browser can get the required information what they are looking for.
To check the SQL injection we have to take care of the input fields like text boxes, comments, etc. The Special characters should be either properly handled or skipped from the input.
Cross-Site Scripting (XSS)
Cross-site scripting (also known as XSS or CSS) is a type of computer security vulnerability typically found in web applications. Cross-Site Scripting is one of the most common application layer hacking techniques. Cross-Site Scripting is a vulnerability in web applications that allows an attacker to inject HTML and JAVASCRIPT code into a web page. This type of attack is injecting malicious scripts into victim’ web browsers. These malicious scripts are used to steal the vital information stored in the cookies.
Types of testing to perform while Security Testing
Let’s discuss what all steps to prepare while preparing and planning for Security testing:
- The first step is to understand the business requirement, security goals, and objectives in terms of security compliance of the organization. The test planning should consider all security factors like Organization might have planned to achieve PCI compliance etc.
- Understand and analyze the requirements of the application under test.
- Collect all system setup information used for the development of Software and Network like Operating Systems, technology, hardware.
- Make out the list of Vulnerabilities and Security Risks.
- Based on the above step prepare a Threat profile.
- Based on identified Threats, Vulnerabilities and Security Risks prepare test plans to address these issues.
- For each identified Threat, Vulnerabilities and Security Risks prepare Traceability Matrix.
- All security testing cannot possible to execute manually, so identify the security testing tools to execute all security test cases faster & more reliable.
- Prepare the Security tests case document.
- Perform the Security Test case execution and retest the defect fixes.
- Execute the Regression Test cases.
- Prepare a detailed report of Security Testing which contains Vulnerabilities and Threats contained, detailing risks, and still open issues, etc.
⇓ Subscribe Us ⇓
If you are not regular reader of this website then highly recommends you to Sign up for our free email newsletter!! Sign up just providing your email address below:
Happy Testing!!!
- Seven attributes of Security Testing
- Understand SQL Injection Better with the SQL Injection Cheat Sheet
- What is Exploratory Testing?
- What is Globalization and Localization in Software Testing?
- Tutorial 2: Introduction to Mobile Testing Application
- What is a Crowdsourced Testing?
- Attributes And Types Of Security Testing – Basic Fundamentals
- How To Do Security Testing Using SoapUI?
- How To Test Responsive Website – Sample Test cases and Examples!!
- Essential Elements in the IoT Software Testing


2 thoughts on “Security Testing approach for Web Application Testing”
Hi.. Guys.. anyone can u tell me how web testing is carried in an MNC what are the steps to be follow for the manual testing
Hi,
Could you tell me what is the best tool for security testing and provide the study doc also.
With Regards,
Jagadishwar